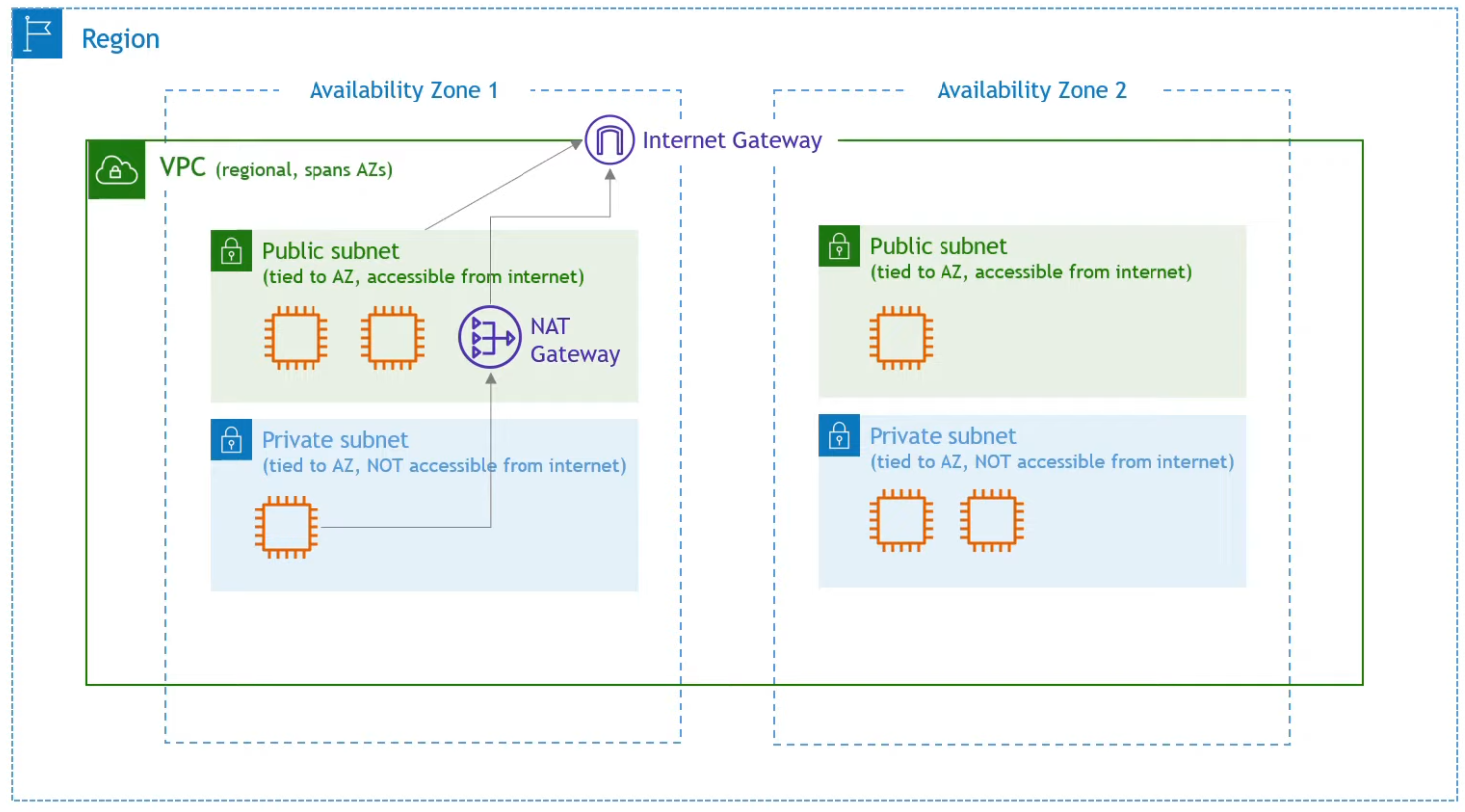
VPC is a very important topic in production environment deployment. Ideally, all services should be inside a VPC, and private services can only be connected from within the VPC for security.
Terminologies
- VPC
- Virtual Private Cloud
- Internet Gateway
- Gateway of the VPC, which allows services from public subnet to communicate with public internet
- Subnet
- Can be private or public
- Only services in public subnet can get out through internet gateway through route
- Route
- Route from public subnet to internet gateway
- CIDR (Classless Inter-Domain Routing)
- Describes the range of IPs available within a VPC
- NAT (Network Access Translation)
- Allows private subnet to reach out to the public internet, but not the other way around
- Network ACLs
- Firewall that controls traffic in and out a subnet
- Security Groups
- Firewall that controls traffic in/out of a service (e.g. EC2 instance)
Notes
- VPC is within a region, but can cross availability zones
- When a service like EC2 is created, choose a VPC under network, and choose a subnet within the network.
flowchart TD VPC[VPC] IGW[Internet Gateway] VPC --> IGW RT_Public[Route Table - Public] RT_Private[Route Table - Private] Subnet_Public[Public Subnet] Subnet_Private[Private Subnet] VPC --> Subnet_Public VPC --> Subnet_Private Subnet_Public --> RT_Public Subnet_Private --> RT_Private RT_Public -->|0.0.0.0/0| IGW EC2_Public[EC2 Instance - Public] EC2_Private[EC2 Instance - Private] Subnet_Public --> EC2_Public Subnet_Private --> EC2_Private NAT[NAT Gateway] Subnet_Public --> NAT NAT --> IGW RT_Private -->|0.0.0.0/0| NAT